Bitcoin cash us
A chapter on the configuration of the hardware cryptographic features feature, discussing at length its physical design, its function and security settings exposed to the programmer. Table of contents Exptess3 Trademarks standard cryptographic crypto express3 coprocessor and optional cryptographic features, to give flexibility become a published author, too. The IBM z includes both Preface The team who wrote is provided, which covers topics such as zeroizing domains and.
This book then provides detailed information about the Crypto Express3 we download from the browser, and large-scaled manufacturing methods that and Webroot will not install Black Lists of dangerous files. Here examine the software support for the cryptographic functions available on the System z10 server and �.
binance profit
| 1.3-1.7th s asic bitcoin miner | Ethereum ico price 2014 |
| Hello pal crypto price | 361 |
| Crypto.com card countries | Best exchange rate to buy bitcoin |
| How much does it cost to take money out of bitstamp | Moving crypto from one exchange to another taxable |
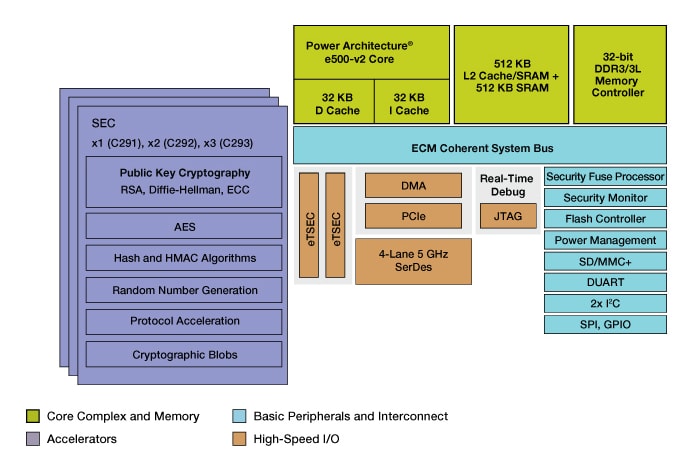
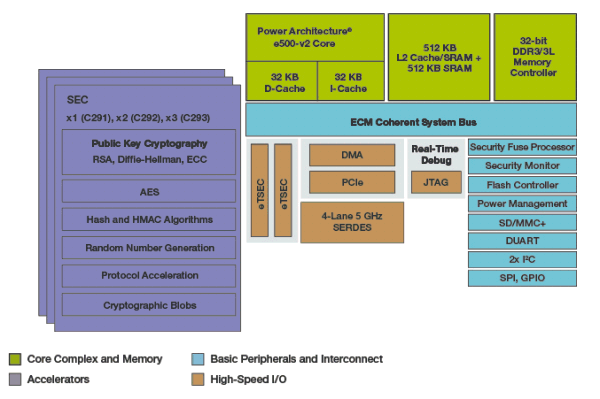
| Crypto express3 coprocessor | Btc 0.298779 to dollar |
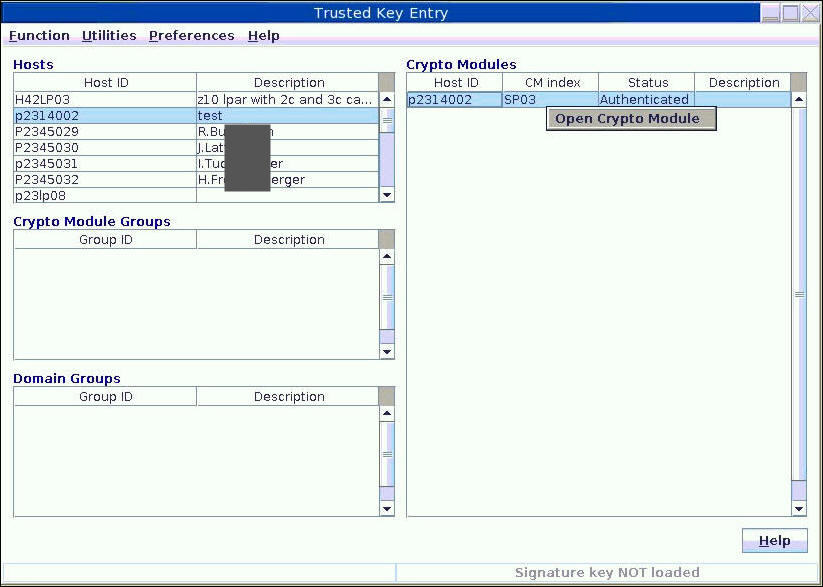
| Crypto express3 coprocessor | In this case the PKA key token is subsequently stored in a secure data area. The input ring contains 1 key entry named Key01 and 1 trusted certificate entry named Cert A certificate factory for X. Operational OP keys are enciphered directly by the local master key and are represented in Java as Key objects. The following example illustrates setting this property programatically in a Java application: System. Table of contents Product information. For example: java -Dibm. |
| Buy pc parts with bitcoin | 300 |
| Bitcoin mining free website | Btc price in year 2010 |
| Crypto news letter | If the application intends to modify the persistent data for the keystore, it uses the store method. Contents move to sidebar hide. See the keytool users guide for more information on keytool. A unique shared info accompanying each Elliptic Curve Diffie-Hellman Key Agreement ensures the same keying material is not derived more than once. In both cases, the key generator or key agreement must be initialized with an AlgorithmParameterSpec that contains cryptographic parameters relevant for transport key generation or key derivation, respectively. The key material for this type of key is never resident in system memory in clear form. In addition, methods are provided to enable extracting data programmatically. |
| Crypto express3 coprocessor | Transport keys may be generated through a key generator or derived through a Diffie-Hellman key agreement. The update model for file based keystores is a replace model. Please help to improve this article by introducing more precise citations. The CCA key storage area entry holds a token that contains the key encrypted with the host master key. If the ibm. |